What is OAuth 2.0?
OAuth 2.0 is an open-standard authorization framework that allows third party services to safely permit authenticated access to their assets without sharing critical login credentials — i.e., the user's password.
OAuth works on the principle of granting permission to access data rather than providing proof of identity, meaning it is an authorization protocol rather than an authentication protocol.
Users delegate exactly what personal information will be revealed. OAuth works over HTTPS, authorizing servers, devices, APIs, and applications. Instead of passwords, it uses short-term access tokens.
OAuth doesn’t share password data but instead uses authorization tokens to prove an identity between consumers and service providers. OAuth is an authentication protocol that allows you to approve one application interacting with another on your behalf without giving away your password.
OAuth Roles:
- Resource Owner: The resource owner is the user who authorizes an application to access their account. The application’s access to the user’s account is limited to the scope of the authorization granted (e.g. read or write access)
- Resource Server: The resource server hosts the protected user accounts and capable of denying or allowing access to the protected resources of the resource owner(s)
- Authorization Server: The authorization server verifies the identity of the user then issues access tokens to the application.
- Client: The client is the application that wants to access the user’s account. Before it may do so, it must be authorized by the user, and the authorization must be validated by the API.
How to create an application in OAuth
Create an login account https://manage.auth0.com.
Note: You can select other types based on your use case.
Select Permissions based on your requirement and click on Authorize.
Settings: Having client ID, client secret, specify call back url and Grant Types
Under Advanced Settings, specify Grant Types..
Please make note of Client ID, Client Secret Token URL and JSON Web Key Set and then apply OAuth on any API.
Under Endpoints, you can see list of URLs.
Please make note of Client ID, Client Secret Token URL and JSON Web Key Set and then apply OAuth on any API.
Here, I have applied it on MuleSoft API.
Login into Anypoint platform and go to API Manager and click on API
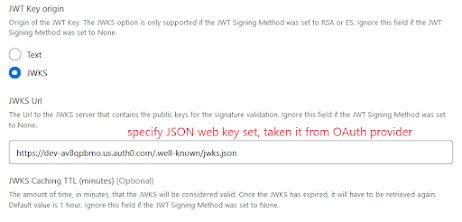
Specify JWKS URL and leave remaining setting ..and save it.
First, get the access token by specifying client id and client secret.
Token URL is available in Oauth application end points tab
Methods is Post and body is client id and secret..etc. These details are available in Quickstart tab.
Now you can see the token in response section.
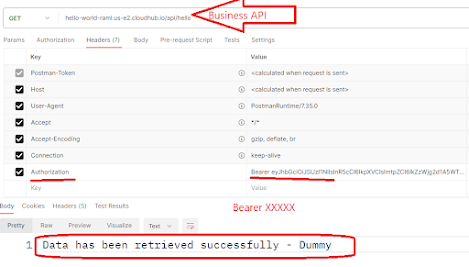
We need to access the API by providing authorization token as the bearer token.
Under Headers> Authorization as Bearer <access token>
Then, you can see the response.
Note:
1. Based on your business requirement, you can disable/enable the API Policy from API Manager (Anypoint Platform).
2. And, you can change grant types and permissions from OAuth(application). In real-time, your infra team will take care of it.
apisec.ai
dzone.com
Thanks for reading. :-)
















No comments:
Post a Comment